Phishing Simulator
Phishing attacks remain one of the top causes of security incidents. Fraudulent emails are becoming increasingly sophisticated, often mimicking trusted sources and bypassing automated filters. As these threats evolve, organisations need a clear understanding of how employees will respond in real scenarios. Since 95% of breaches occur due to human error*, an organisation is most susceptible to a cyberattack due to the negligence of an employee getting phished by a malicious email.
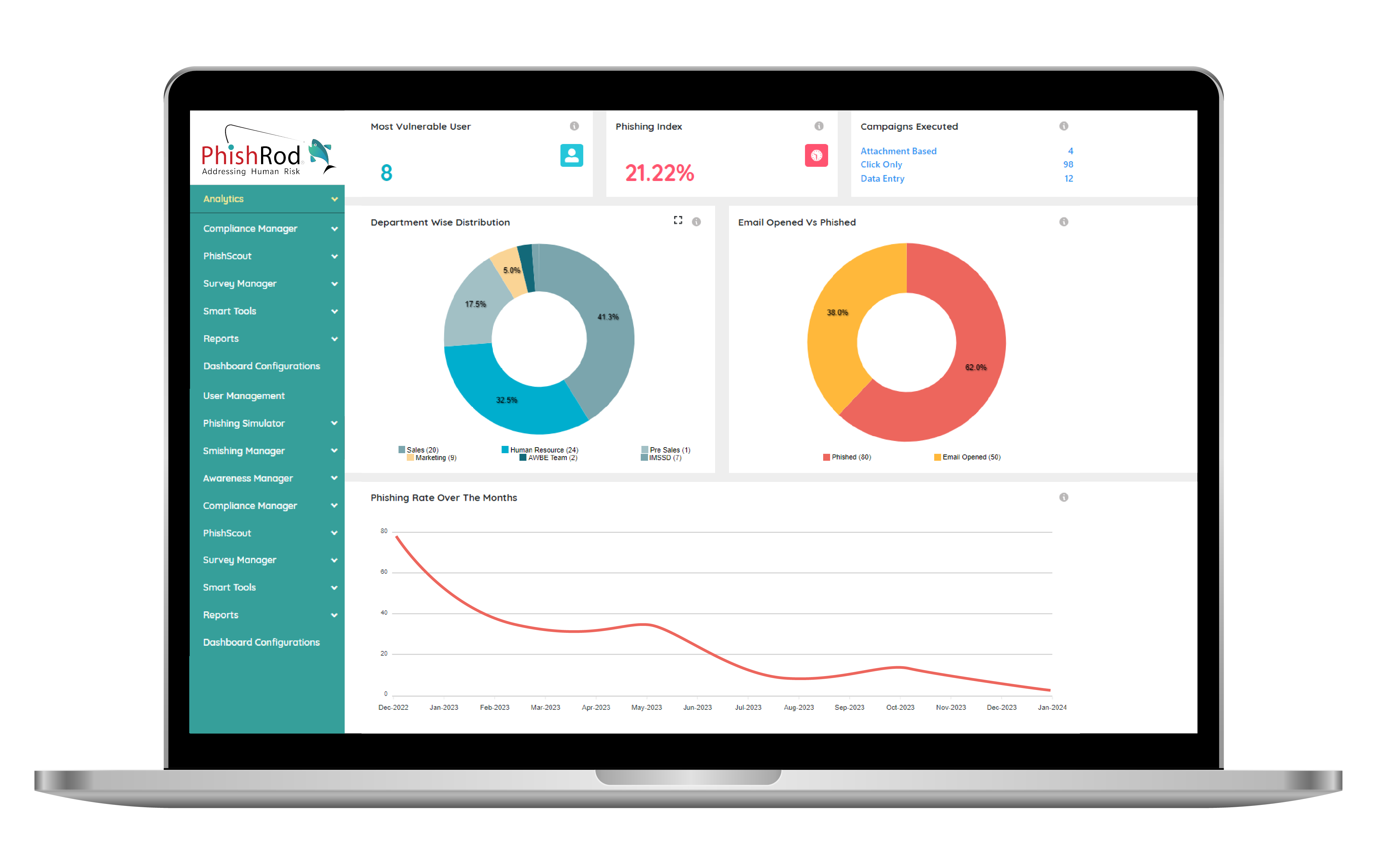
Using Phishing Simulator, PhishRod helps organisations test the phishing readiness of its employees by conducting mock phishing exercises in a controlled environment. This activity then generates a phishing index which helps give a quantitative visibility at individual, department and organisation levels to identify the most vulnerable users.
“ Regular phishing simulations have been shown to increase the likelihood of users reporting real phishing emails by up to 60%. ”
Key Features
Extensive Template Library
Access an extensive library of over 2,000 customisable phishing email templates and scenarios, available in multiple languages to suit your organisation’s context and user base.
USB Phishing, Vishing & Smishing
Train users across multiple threat vectors to build resilience beyond email-based threats including smishing, vishing and USB phishing.
Instant Awareness
Redirect phished users to contextual awareness content like microlearning videos and interactive infographics. Reinforce key security concepts in real-time.
Traceable Learning Points
Share computer-based awareness training modules with phished users through Security Awareness Manager and track progress based on whether they complete, attempt or fail the training module.
Customisable Landing Pages
Fully customise landing pages after each simulation to deliver targeted security messages and drive behaviour change.
Diverse Template Types
Train your team to recognise and respond to a wide range of phishing scenarios like data entry, click-only, attachment-based, link-based and double-barrel phishing.
Multi-Template Campaigns
Deliver different phishing templates within a single campaign, targeted for different user groups for effective testing.
Campaign Approval Workflow
Use structured workflows with built-in maker and checker roles to ensure phishing campaigns are reviewed and approved in line with internal protocols.
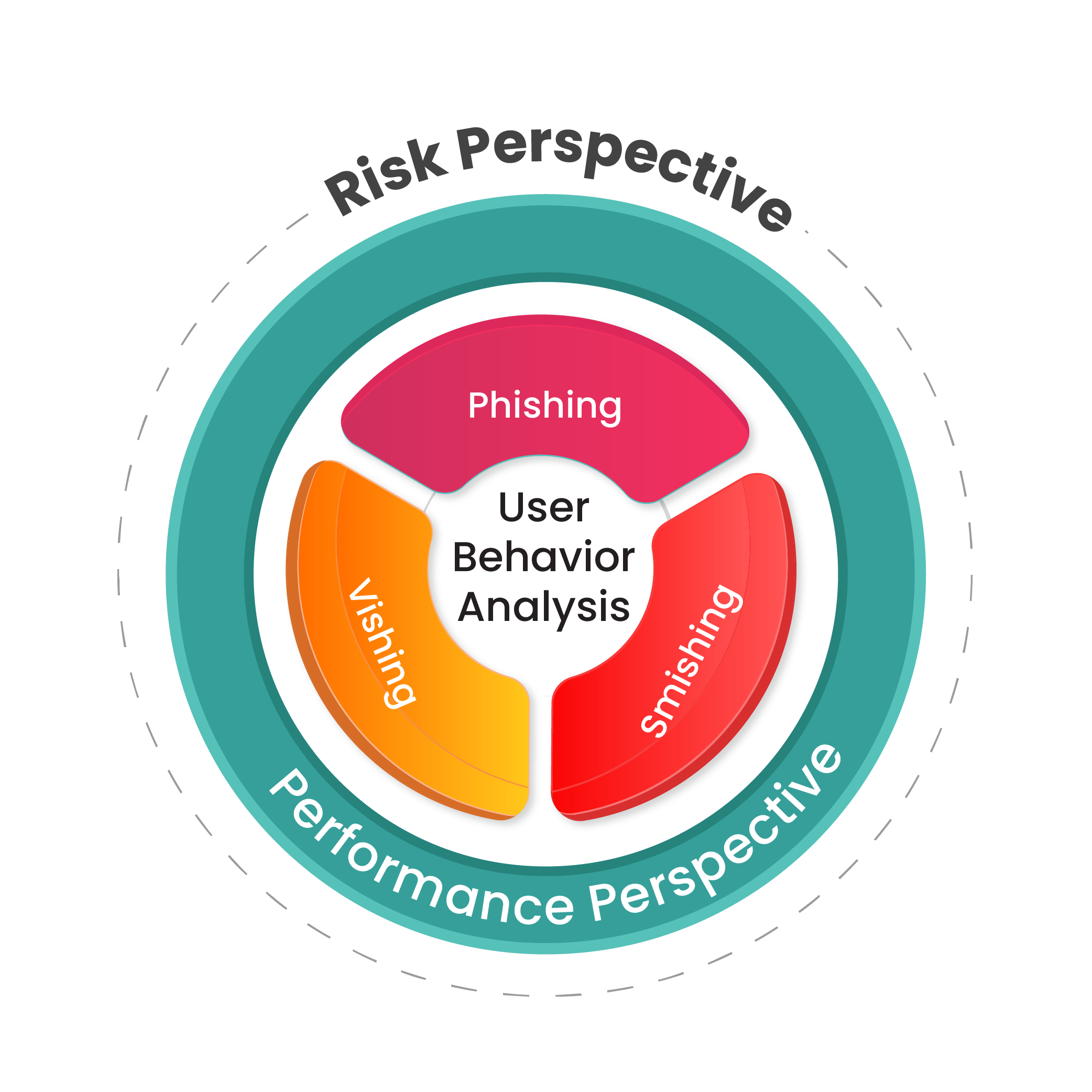
How it Works?
Phishing Simulator enables you to run realistic phishing campaigns in a controlled environment. Our simulations reflect evolving phishing tactics including Smishing, Vishing and USB Phishing to help evaluate user awareness and response behaviour.
Each campaign tracks key actions such as link clicks, credential submissions, and whether the email was reported. This gives you clear visibility into user risk and reveals behavioural patterns that may need attention.
By analysing simulation results, organisations can identify high-risk individuals, track improvement over time, and align training efforts with actual behaviour. This helps reduce phishing risk before real threats materialise.
Key Benefits
Extensive Library of Pre-Built Simulations
Access over 2,000 ready-to-deploy phishing scenarios to train employees with real-world attack vectors.
Tailored Simulations for Targeted Training
Customise phishing campaigns to mirror industry-specific threats and regional risk profiles for maximum relevance.
Data-Driven Insights from Every Campaign
Track performance and uncover behavioural trends to continuously strengthen your security awareness efforts.
Case Studies

Preventing Cybersecurity Threats with Phishing Readiness and End User Awareness
One of the largest banks in Qatar found itself under the impeding threat of cyberattacks. In today’s digital age, where the disclosure of sensitive financial information due to cyberattacks is unfortunately common, a new breed of cyber threats has emerged, characterized by their sophistication and rapid evolution. These evolving threats have left every organization vulnerable to potential breaches.

Revolutionizing Digital Resilience with Cyber Security Awareness Program Automation
This PhishRod client is one of the largest hospitals in the Kingdom of Saudi Arabia. With over 17,000 employees, they have branches across 4 major cities in the Kingdom. PhishRod was selected by the customer to automate the security awareness program and policy compliance to empower its end users against phishing attacks.
Validated by our Customers