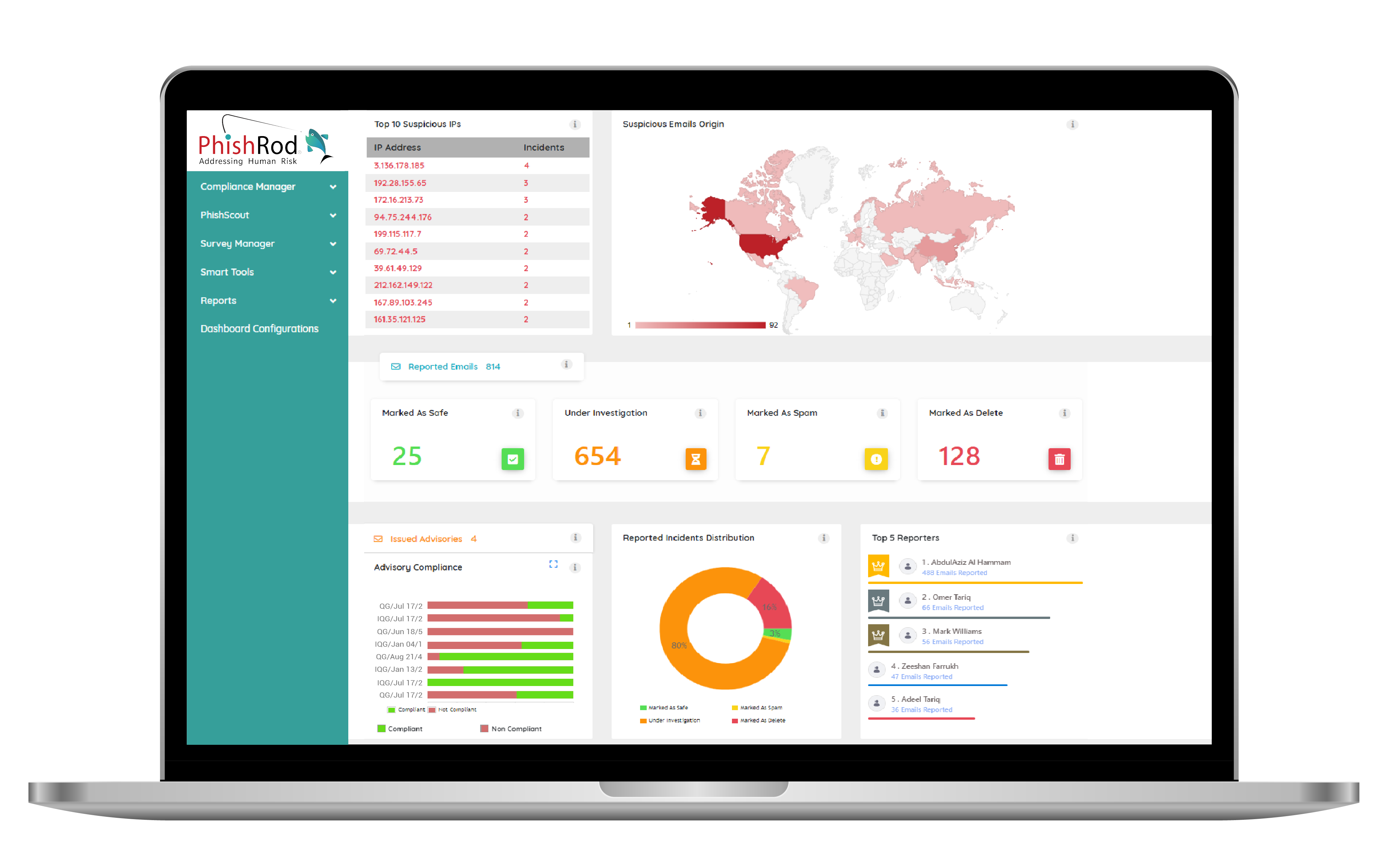
PhishScout
Security controls such as IPS & Email Gateways are only effective to a certain extent. This is why phishing remains the most potent threat vector to date. PhishScout is an automated phishing defence & orchestrated response that allows the IT security teams to instantly investigate suspicious emails with the ability to quarantine and ultimately delete phishing emails from the end user’s mailbox.
PhishScout uses built-in 150+ threat intelligence feeds to help IT security teams analyse reported suspicious emails. Third Party threat intelligence feeds can also be integrated for enhanced detection capabilities helping organisations automate their phishing incident response and to instantly thwart a phishing attack. The automated & orchestrated response workflow ensures role-based coordination between relevant stakeholders to report, investigate, quarantine and delete phishing emails from the end user’s mailbox in the shortest possible time.
“ PhishScout enables automated triage and categorisation, reducing SOC workload by 40%. ”
Key Features
Automated & Orchestrated Incident Response
Leverage 150+ threat feeds to analyse, quarantine, and delete phishing emails instantly through a coordinated response workflow.
SIEM Integration
Utilise the ability to share the incident investigation details with the existing SIEM solution using native APIs.
SOAR Integration
Integrate with your existing SOAR solution to perform remedial actions.
Polymorphic Detection Rules
Use adaptive detection rules to mitigate the ever-evolving phishing tactics.
Converting Phishing Emails into Simulation Templates
Train employees on real-time threat vector by converting real time suspicious emails into phishing templates.
Advisory Campaigns
Create automated advisory campaigns based on real-time Indicator of Compromise (IOCs) and educate users to build cyber resilience.
How it Works?
Once a suspicious email is reported, PhishScout extracts the links & attachments from the reported suspicious email and performs IP Scanning, Domain Reputation Scanning, URL Scanning, Site Verification, Attachment Scanning using 150+ intelligence feeds and creates an incident. Based on the provided evidence, the Primary and Secondary analysts work in tandem using role-based access to coordinate threat neutralisation and determine whether to ignore or delete the quarantined email from all mailboxes.
Key Benefits

Reduced Remediation Time for Phishing Incidents
Streamline your phishing incident response workflow by reducing remediation time.

Human-Centric Approach to Mitigate Residual Risk
Empower end users to mitigate the risk that bypasses existing technology and email gateway.

Centralised Threat Intelligence Dashboards
Real-time insights and analyses into phishing activity, origin of the threat sources and user engagement all in one centralised dashboard
Case Studies

Addressing the Human Risk & Building a Cyber Secure Culture for One of the Leading Banks
A leading bank in Egypt wanted to address the human risks from cyber security perspective. They intended to build a cyber security awareness program with an objective to transform end user behavior. Besides being an internal initiative, the bank had to comply to the guidelines provided by the Central Bank of Egypt as well as Egypt Financial Cyber Security Framework.

Enhancing Cybersecurity Resilience with Automated Defense Against Phishing
For an organization that is one of the largest oil & gas giants of Texas, a market leader, and employs 70,000+ employees, it became increasingly difficult to protect their workforce from rising cyberattacks. Phishing attempts and other cyberattacks started disrupting their operations, so a need for an efficient and swift phishing defense mechanism arose.
Validated by our Customers