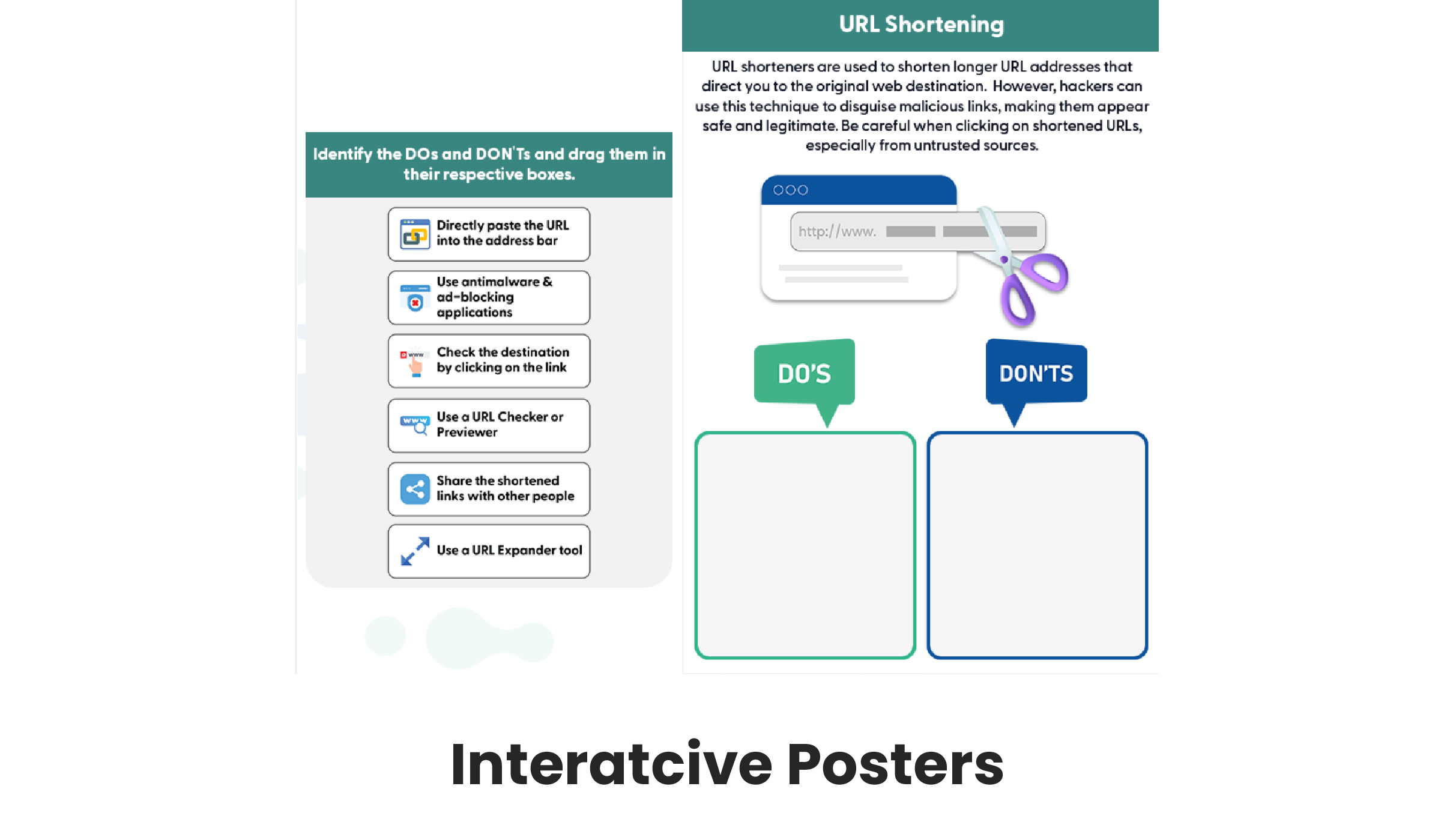
Content Customization
In the ever-evolving landscape of cyber threats, security awareness content must be relatable to end users to ensure better understanding and behavior transformation. Effective cybersecurity awareness cannot follow a one-size-fits-all approach.
Custom Content + delivers content specifically tailored to distinct regional and organizational requirements. Client-specific customisation goes beyond the mainstream awareness approach, delivering content that mirrors the end user’s everyday environment revolving around cyber threats.

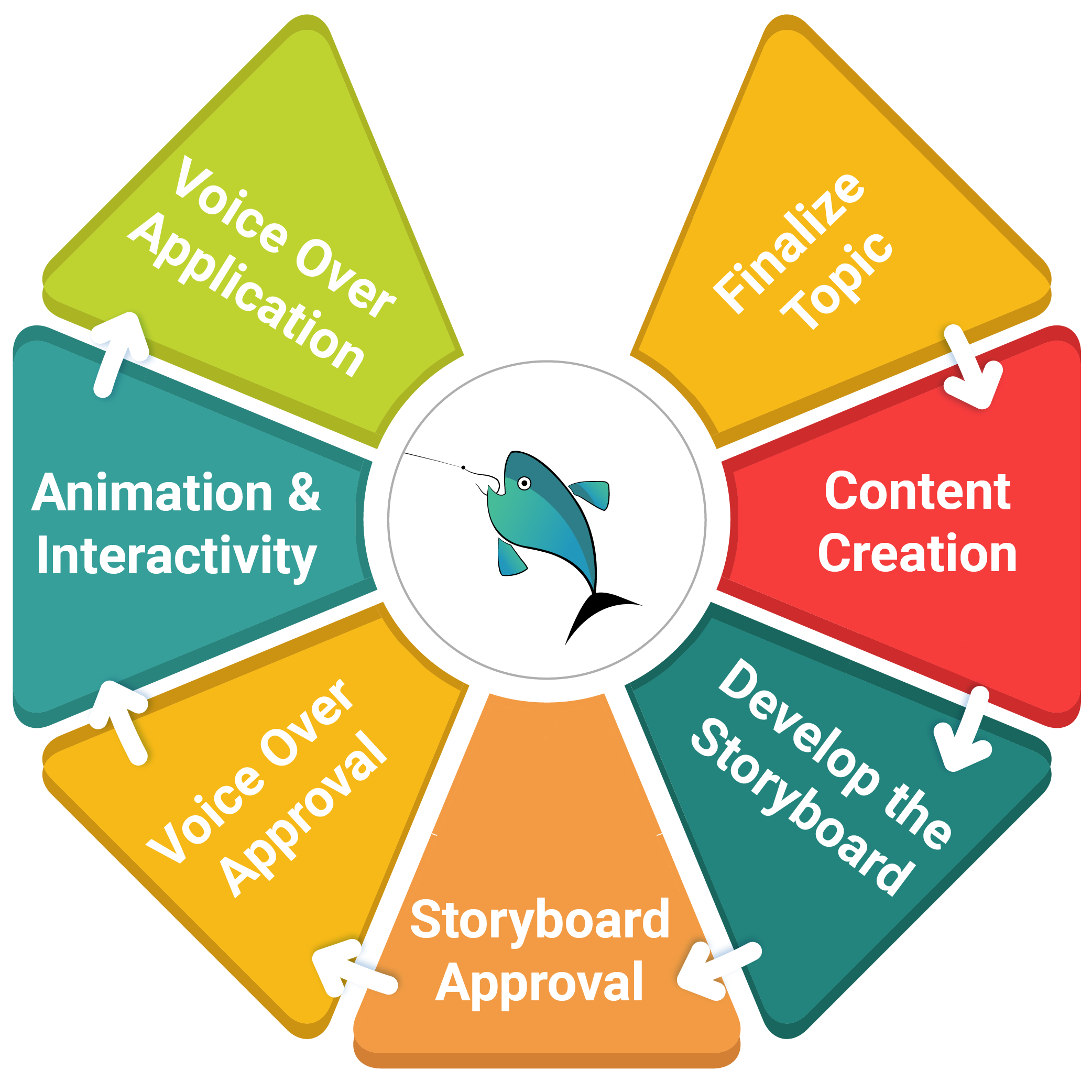
How it Works?
Our approach to customise content is built on a collaborative, step-by-step process. Each module combines clear messaging, real-life context, and interactivity embedded with regional context for relatability. It starts with identifying the topic in consultation with the client followed by content development by our teams. Once initial feedback is reflected, we then move onto visualisation through storyboarding and animation. Voice-overs are added in the required languages, and the final product is delivered in a format that’s easy to engage with. The result is role-specific instructional module that fits into end users’ day-to-day work activities.
With Custom Content +, organizations get access to completely tailored content covering the following aspects:
Branding & Theme
Role-Based Content
Multilingual Adaptation
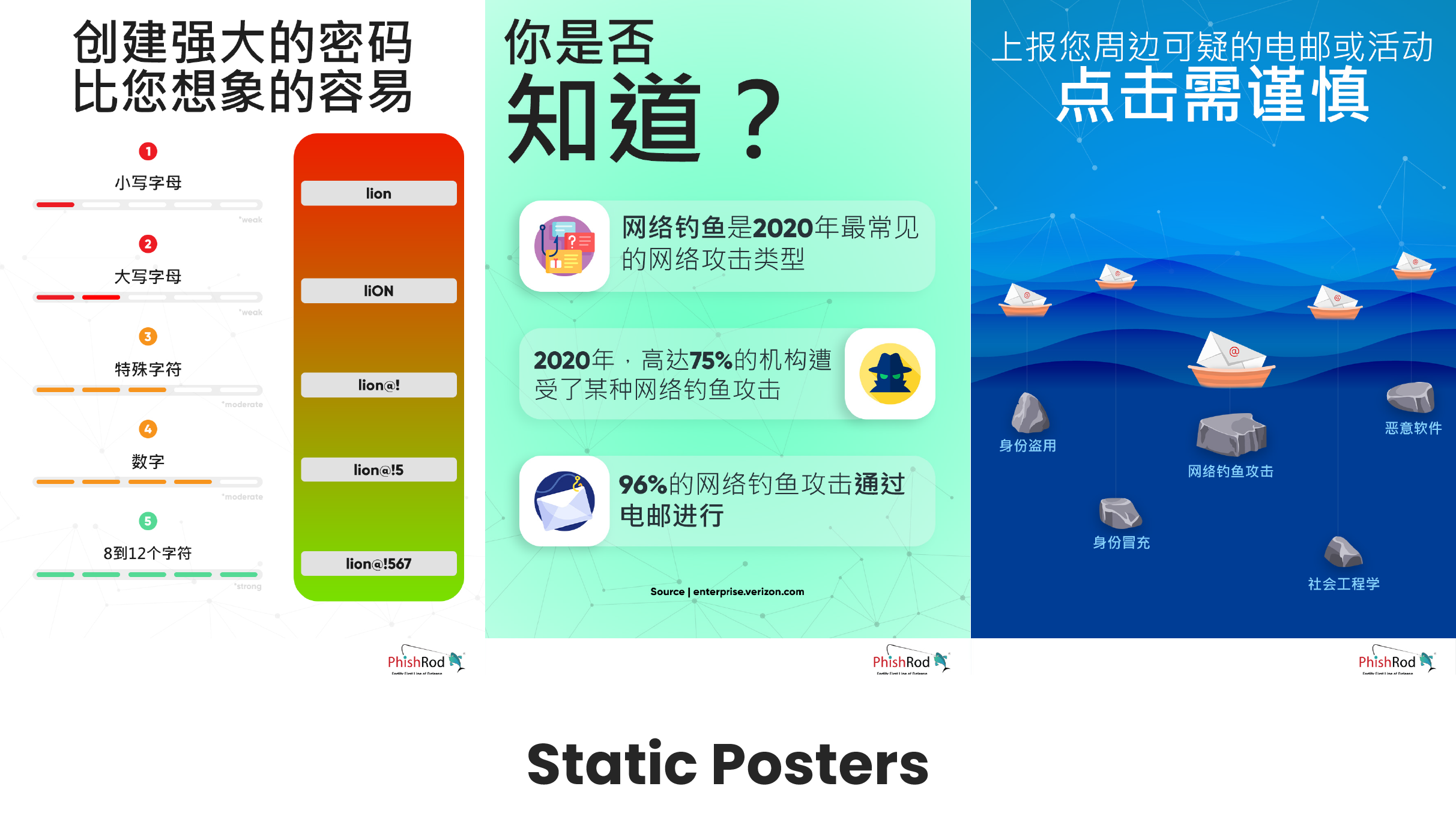
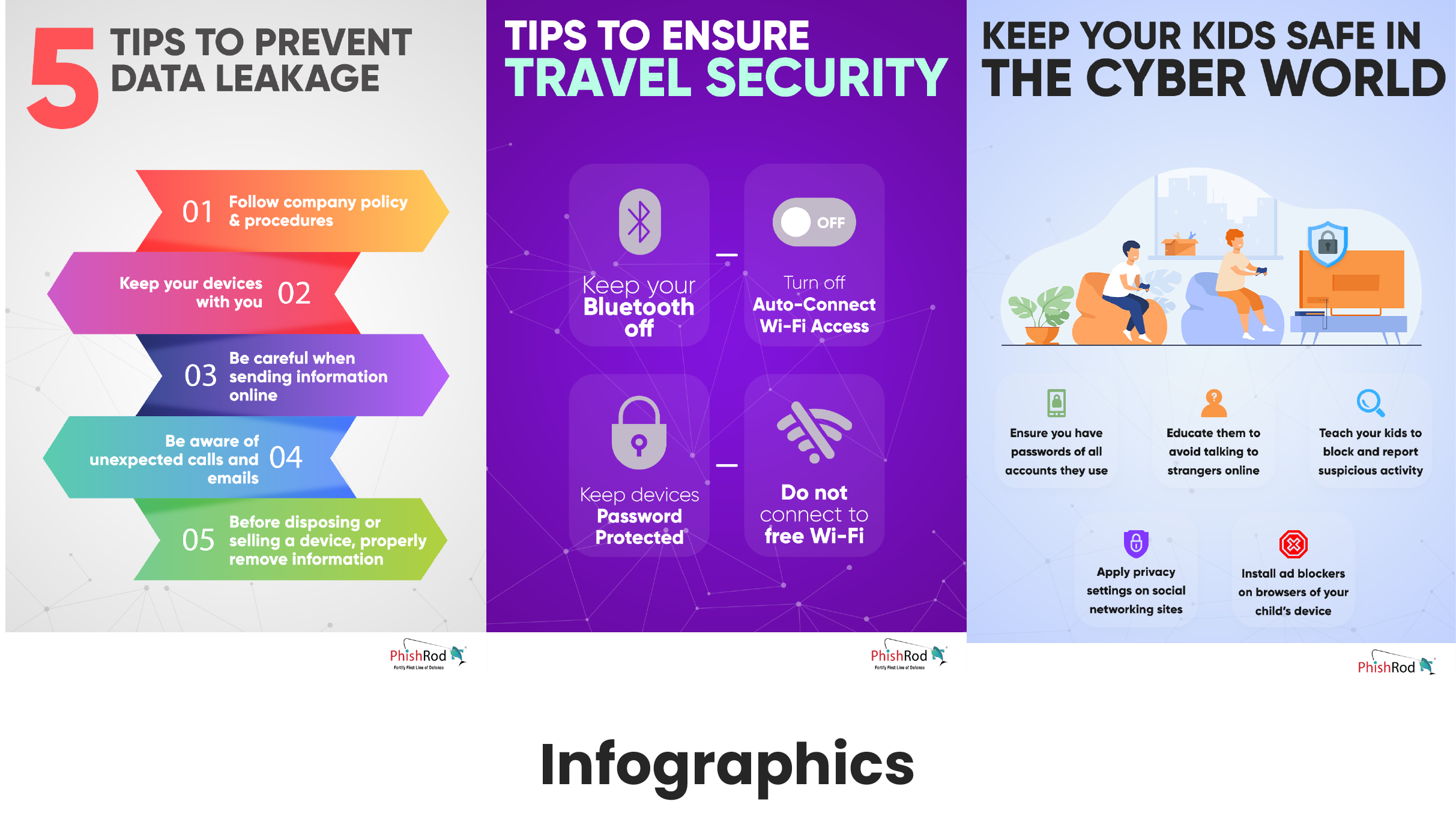
Localised Storyboards
Industry-Specific Customisation
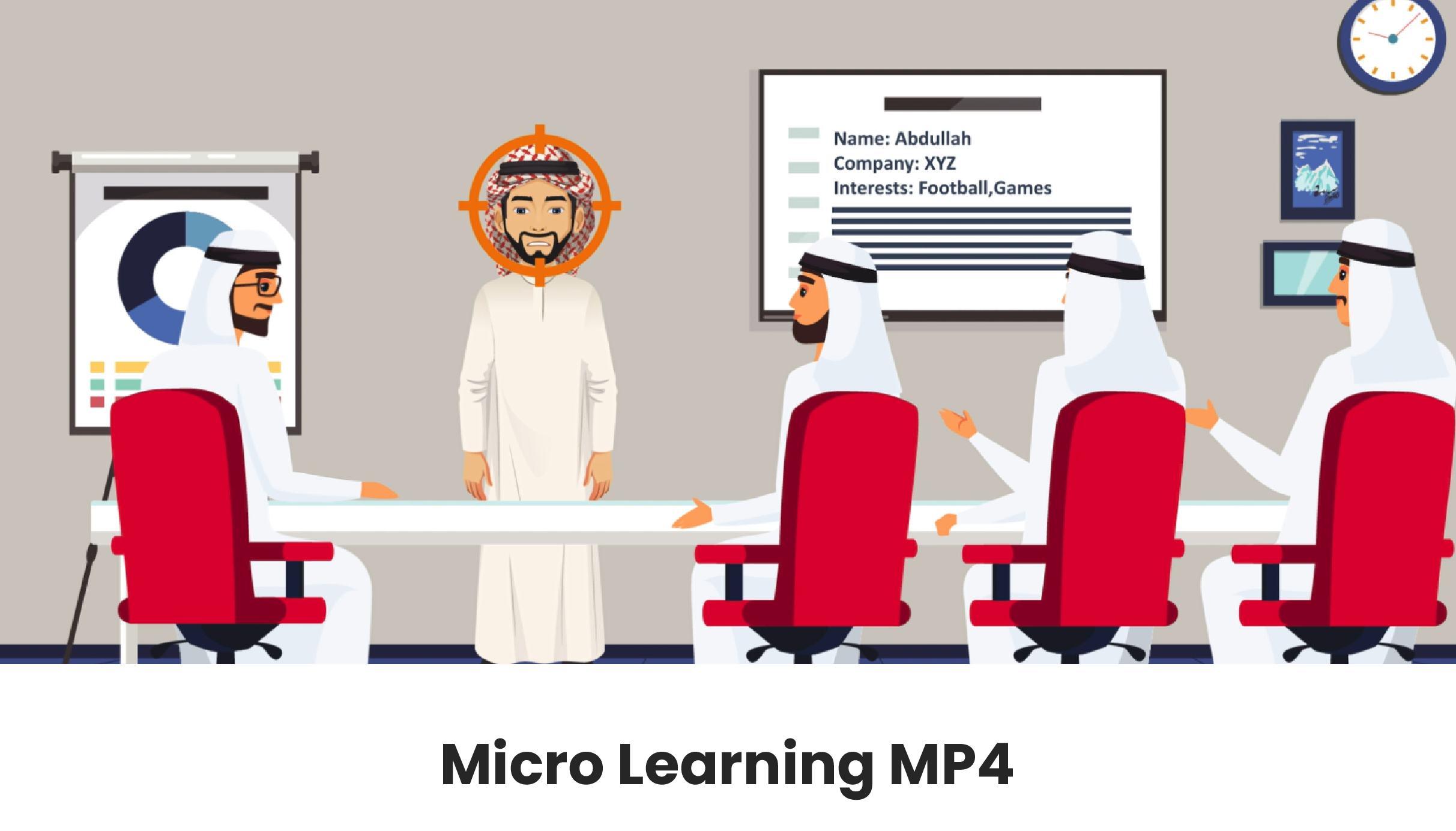
Localised Characters
Key Benefits
Increased User Engagement
Tailored content resonates with employees’ specific environments, making cybersecurity training feel relevant and encouraging active participation.
Higher Training Effectiveness
Collaborative development ensures training accurately addresses real challenges faced by users, leading to meaningful behaviour change.
Efficient Learning Experience
Short, focused modules with clear messaging reduce training fatigue, helping employees quickly grasp and apply crucial cybersecurity skills.
Case Studies

Empowering End Users to Thwart Cyber Attacks
This oil refinery had almost all the technology-based controls including Next-Generation Firewalls, Intrusion Detection & Prevention System (IDPS), and Email Gateways. Despite all these technical security controls, their end-users continued to receive phishing emails. The organization had policies on information security but had no visibility of their compliance by end users.

Addressing the Human Risk & Building a Cyber Secure Culture for One of the Leading Banks
A leading bank in Egypt wanted to address the human risks from cyber security perspective. They intended to build a cyber security awareness program with an objective to transform end user behavior. Besides being an internal initiative, the bank had to comply to the guidelines provided by the Central Bank of Egypt as well as Egypt Financial Cyber Security Framework.